
Security
Securing your business is a primary priority. Beginning from basic Network & Infrastructure Security layers like firewalls and working to secure against more complex Cyber Security threats, an area which businesses can no longer ignore or leave to chance. Australian Mid-Market customers are recognizing the importance of securing their business and ensuring its longevity.
Cyber-attacks are increasing rapidly as hackers develop smarter methods, technologies, and more complex schemes. The financial and brand impact from a cyber-attack or a breach of compliance can be devastating to any organisation, in most cases leading to a huge financial loss or even a complete shutdown of a business. Traditional cyber security solutions are outdated and can be easily circumvented.
Shall we mention the customer data importance and legalities consequences ?
Logic Stream has mastered the 7 layers of Security. We demonstrate our expertise in protecting your systems, data and ensuring your business adheres to the compliance regulations.
- Information Security Policies
- Physical Security
- Secure Networks and Systems
- Vulnerability Programs
- Strong Access Control Measures
- Protect and Backup Data
- Monitor and Test Your Systems
Error: Contact form not found.
We work with our clients to ensure they are provided with a comprehensive and easy to understand view of their environment. We highlight areas of strength and volubility’s tailoring our recommendations to meet our customer’s budgets.
As it is our mission to “help Mid-Market Australian businesses achieve Enterprise grade ICT security”, we more often than not provide our clients with added benefits without additional charges.
Our Security solution deliverables are structured around five pillars:
Each category contains a broad range of solutions. Logic Stream will work with your business to simplify the approach and provide you with a guided path on how to protect your key assets with a minimum investment. Our solutions include:
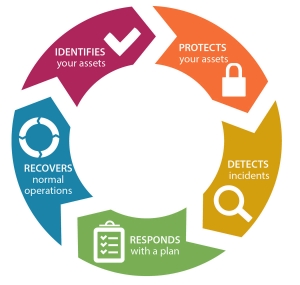
-
- Gap Analysis
- Risk Management
- Asset Management
- Security Auditing
- ISMS
- Security Compliance(g. E8, ISO, PCI-DSS)
- Identify & Privilege Access Management
- Security Education
- Simulated Phishing
- Network Segmentation
- Firewall Management
- DDoS Solutions
- Data Classification
- Application Whitelisting
- Endpoint Security
- Secure Remote Access
- Systems Hardening
- Microsoft 365 Security
- Email Security
- Patch Management
- Data Encryption
- Zero-Trust Solutions
- Security Automation
- Vulnerability Management
- Gap Analysis
- Security Auditing
- SIEM & Log Monitoring
- Dark-Web Monitoring
- Intrusion Detection System
- Application Whitelisting
- Endpoint Security
- Security Automation
- Penetration Testing
- Red-Teaming
- Managed Security
- Incident Response
- Forensics
- Intrusion Prevention System
- Firewall Management
- DDoS Solutions
- Data Loss Prevention
- Email Security
- Backup
- Disaster Recovery
- Business Continuity
- Fail-over Testing
It all starts with an obligation free assessment
Our focus is to deliver “Business outcomes through ICT Solutions”.
Contact us to organise a complimentary consultation. We will take the time to understand your business requirements, provide you with insights, demonstrate the value we can add and conduct a no-commitment assessment on which we base our solution.
Schedule now on Phone Number or by completing the form here.
